‘ADM Power’: Power Tools for Citrix ADM

Hi everyone, I know it’s been a while but I figured this post would be one of those ‘better late than never’ types where readers can hopefully forgive me in exchange for a shiny new utility that I created and felt was useful enough to share!
Without further ado I give you ‘ADM Power‘, a forms-based PowerShell script that automates and simplifies a lot of Citrix ADM & ADC tasks in an enterprise environment (i.e. more than a few ADCs).
What is ADM Power?
As the name implies this PowerShell script uses Citrix’s Nitro APIs to interact with a target ADM, as well as the ADCs it manages, and includes several ‘power tools’ that I’ve started trying to describe in the readme.
The script builds upon and includes modified versions of the functions that I shared in this PowerShell module for Citrix ADM last year, is designed to be self contained, and only requires the ADMPower.ps1 file and ability to run it.. and of course access to a functional ADM 🙂
How do you use it?
Because the script uses Windows form objects to interact with the user, it’s more like a utility than a script. For example, instead of using startup parameters when you launch the script, it prompts you for the relevant details to connect to your ADM instance:
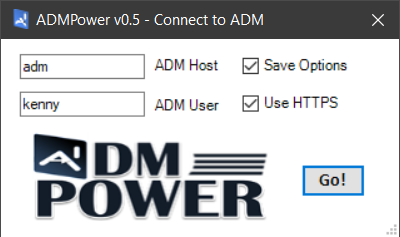
Once connected, you can do lots of ‘stuff & things’ that I’ve added along the way, and can even add your own by reverse engineering my probably not-so-organized script :S
What can it do?
I’ve added a lot of stuff that I find useful, and so there are a lot of things in the readme that I won’t mention here.
That said, I haven’t documented everything that it can do because I tried to make usage as intuitive as possible by leveraging standard GUI elements like labels, toolstrips, and context menus.
For example, you can right-click ADCs to perform common tasks against them, such as logging on in the browser (using the ADM device profile), or opening an SSH or SCP session using prompted credentials:
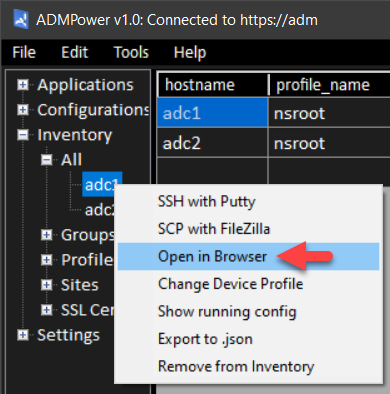

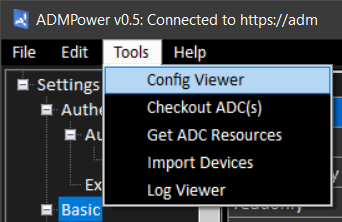
As you can see there are a few other right-click options on ADCs, and there are others elsewhere, particularly in the ‘Inventory’ and ‘Configurations’ sections, as well as a collection of Tools in the menu bar:
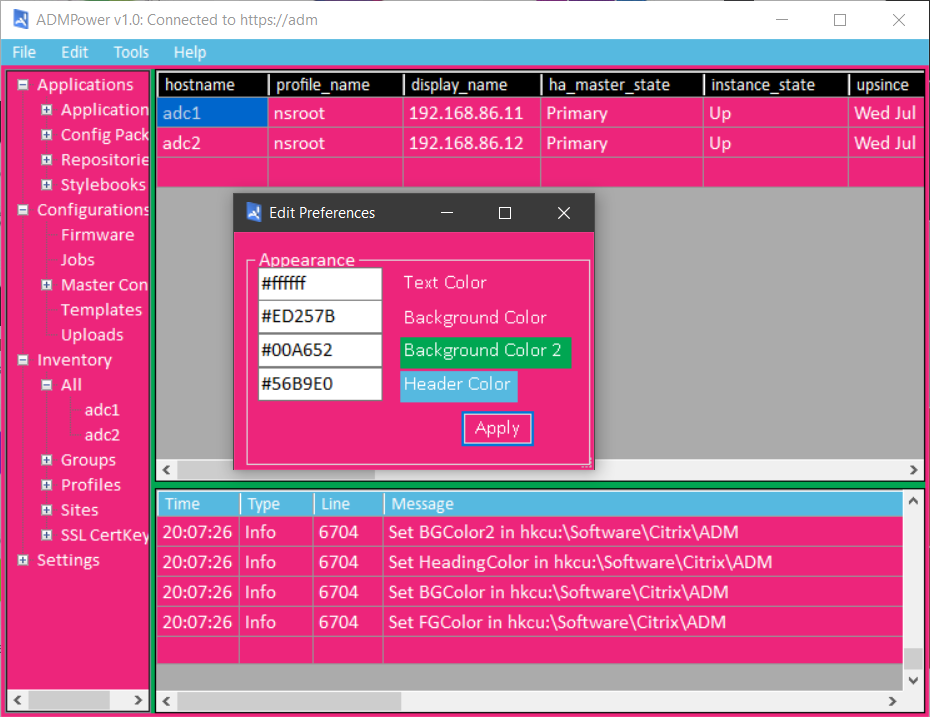
I even added an ‘Edit>Preferences’ form so that you can make ADM Power look the way you like!
Why is Kenny sharing this?
The reason I wrote this in PowerShell was to give anyone who can run it the opportunity to use it while also giving those who can edit and/or write scripts (or use tools like poshgui) the ability to use or extend whatever parts they find useful.
In return I’d ask that if you use this script you give credit where it’s due, and otherwise help me to make the tool more Powerful by providing useful feedback and/or bug fixes! 🙂
In Conclusion..
I’m still working on documenting everything, but I felt like the readme has enough to get most started. I’d like to emphasize that you should use caution when running any script from the internet, and would checking with your organization’s internal policies before you start using it in a production environment.
In general I would suggest starting with a read-only account if you want to step through it first and get acquainted, but would otherwise say that it reads more than it writes and is mostly safe from accidental screw-ups.. but please be careful regardless.
I plan to keep the utility updated as I add features and/or fix bugs, so please feel free to ask questions and share any feedback you might have.
Thanks! -KB