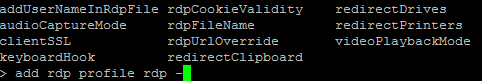
Checking ADC Settings via ADM
Since there seems to be a fair amount of interest in the ADM PowerShell module I shared, and because the recent release of the v19.4.0.34 (1904) of Citrix Workspace App uses a modern ‘Crypto Kit’ (see CTX250104) that requires ECDHE ciphers and ECC curve bindings, I thought I’d share a basic script that leverages ADM’s capabilities as an API proxy to check out NetScaler/ADC configurations.
Using the ADM.psm1 PowerShell module, the following script will generate a .csv list of every ADC in the ADM inventory’s Citrix Gateway vServer ECC curve bindings:
Param(
[string]$ADMHost = "https://adm.domain.local",
[string]$OutFile = ".\out.csv"
)
$RunningPath = Split-Path -parent $MyInvocation.MyCommand.Definition
Set-Location $RunningPath
Import-Module '.\ADM.psm1' -Force
$ADMSession = Connect-ADM $ADMHost (Get-Credential)
$Output = @()
foreach ($ADC in (Invoke-ADMNitro -ADMSession $ADMSession -OperationMethod GET -ResourceType ns).ns)
{
$vServers = (Invoke-ADMNitro -ADMSession $ADMSession -OperationMethod GET -ResourceType vpnvserver -ADCHost $ADC.ip_address).vpnvserver
foreach ($vServer in $vServers)
{
$ECCBindings = (Invoke-ADMNitro -ADMSession $ADMSession -OperationMethod GET -ResourceType sslvserver_ecccurve_binding -ResourceName $vServer.name -ADCHost $ADC.ip_address).sslvserver_ecccurve_binding
foreach ($Binding in $ECCBindings)
{
$ExportObject = New-Object PSCustomObject -Property @{
'ADC Name' = $ADC.hostname
'ECC Curve' = $Binding.ecccurvename
'vServer' = $Binding.vservername
}
$Output += $ExportObject
}
}
}
$Output | Export-Csv $OutFile -NoTypeInformation
Invoke-Item $OutFile
If you were following along, and everything went well, your associated .csv viewer should show you the results:
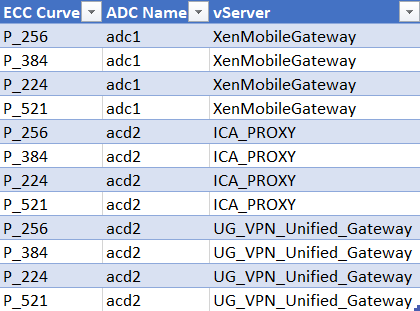
One of the great things about using ADM as an API proxy is that it takes care of organizing ADCs, which makes scripted interactions much more manageable, especially when you’re dealing with a global deployment of ADCs (i.e. ‘more than a few’).
Taking this further, if I wanted to only target a specific device group in the above query I could filter the ADC list by first getting the device_group object with name = “Group1”, which can be passed to Invoke-ADMNitro -Filters as a hashtable:
$Filter = @{
name = "Group1"
}
$DeviceGroups = (Invoke-ADMNitro -ADMSession $ADMSession -OperationMethod GET -ResourceType device_group -Filters $Filter).device_group
foreach ($Device in $DeviceGroups.static_device_list_arr)
{
$vServers = (Invoke-ADMNitro -ADMSession $ADMSession -OperationMethod GET -ResourceType vpnvserver -ADCHost $Device).vpnvserver
foreach ($vServer in $vServers)
{ ...
You can then use the array of device IP addresses, instead of all ADCs, to check against.
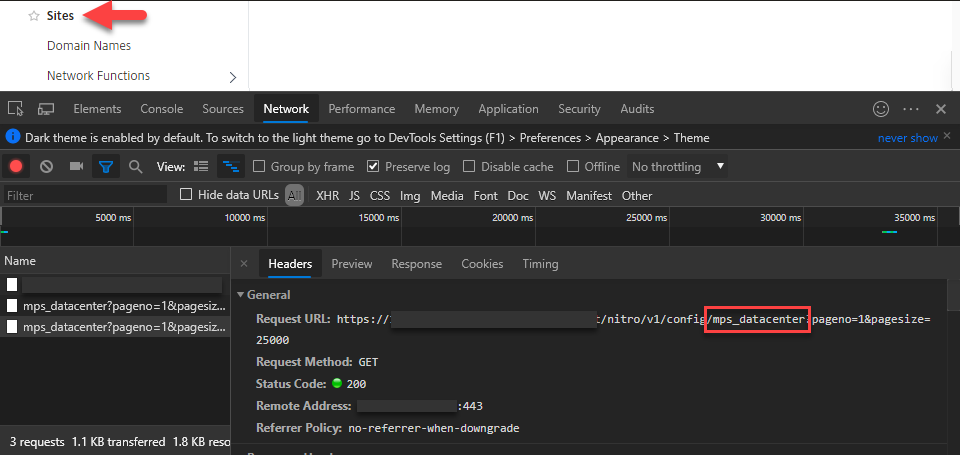
Similarly, you could do the same using by region or ‘Sites’ (e.g. Datacenters) if you’ve populated them in ADM, or using a wildcard match on the filter. If you’re ever unsure about what the ResourceName or filter should be, just open your F12 debug tools in Chrome and inspect the requests in the network tab:
Similarly, you can always download the API docs and/or SDK from the ‘Downloads’ section in ADM, which I prefer to view the C# API SDK in DotPeek:
Anyways, I’ll try to share other examples as I get time, but hopefully this was useful for someone out there!